When you work with Azure VMs in the same virtual network, the name resolution between them is automatically made by the Azure-provided name resolution service. When you deploy VMs in different virtual networks or role instances in another cloud service, name resolution must be made by a custom DNS service.
Azure DNS Private Resolver is a new service that provides a reliable and secure DNS service for your virtual network. Azure Private DNS manages and resolves domain names in the virtual network without the need to configure a custom DNS solution. By using private DNS zones, you can use your own custom domain name instead of the Azure-provided names during deployment.
Working with Azure SQL VMs, I was trying to configure Linked Services between two SQL Server Instances deployed in different virtual networks, traffic between networks was simple, but if I wanted to use the hostnames instead of the IP addresses, I realized that a DNS Private Resolver was needed.
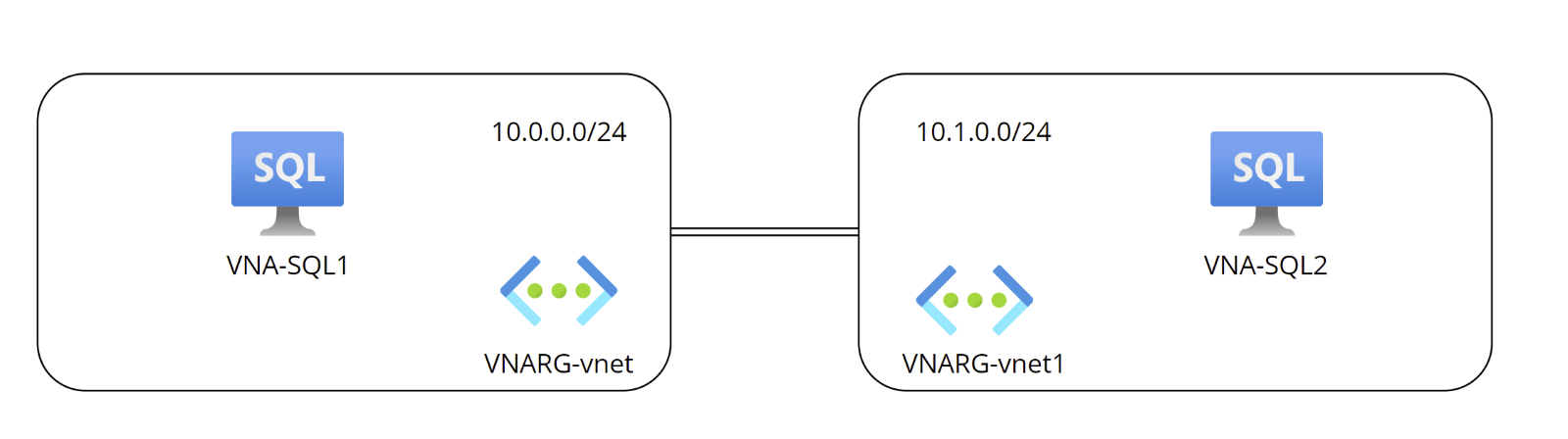
I will describe the steps to configure an Azure DNS Private Resolver using Powershell in the following Azure environment:
|
SQL Virtual Machine |
Resource Group |
Virtual Network |
VM Subnet |
Address Space |
|
VNA-SQL1 |
VNARG |
VNARG-vnet |
10.0.0.0/24 |
10.0.0.0/16 |
|
VNA-SQL2 |
VNARG |
VNARG-vnet1 |
10.1.0.0/24 |
10.1.0.0/16 |
To run the code in this article, I will use Azure Cloud Shell, the interactive environment activated from the Azure portal through a web browser.
To start a Cloud Shell console, select the Cloud Shell button on the menu bar at the upper right in the Azure portal:
Select PowerShell in the left menu, and you will be granted console access:
Creating a New Resource Group
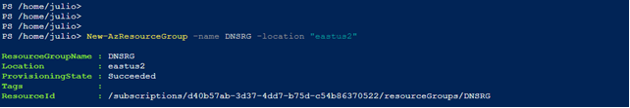
Create a new resource group to store the Private DNS zone:
New-AzResourceGroup -name DNSRG -location "eastus2"
Creating a private DNS zone
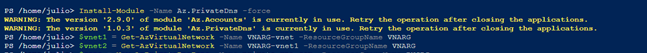
First, install the Az.PrivateDns PowerShell module:
Install-Module -Name Az.PrivateDns -force
Next, capture the information of the two virtual networks to link them to the DNS zone after DNS creation:
$vnet1 = Get-AzVirtualNetwork -Name VNARG-vnet -ResourceGroupName VNARG
$vnet2 = Get-AzVirtualNetwork -Name VNARG-vnet1 -ResourceGroupName VNARG
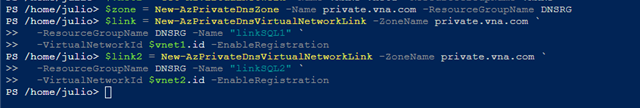
Finally, create the DNS zone with the desired name (private.vna.com) in the DNSRG resource group, link the virtual networks to the DNS zone, and enable automatic registration.
The -EnableRegistration parameter will automatically register all hostnames inside each virtual network.
$zone = New-AzPrivateDnsZone -Name private.vna.com -ResourceGroupName DNSRG
$link = New-AzPrivateDnsVirtualNetworkLink -ZoneName private.vna.com `
-ResourceGroupName DNSRG -Name "linkSQL1" `
-VirtualNetworkId $vnet1.id -EnableRegistration
$link2 = New-AzPrivateDnsVirtualNetworkLink -ZoneName private.vna.com `
-ResourceGroupName DNSRG -Name "linkSQL2" `
-VirtualNetworkId $vnet2.id -EnableRegistration
Registering hostnames and adding DNS records
As we enabled automatic registration during the Networking link, existing VMs in each Virtual network will be registered automatically after creation. We can list the DNS records with:
Get-AzPrivateDnsRecordSet -ZoneName private.vna.com -ResourceGroupName DNSRG
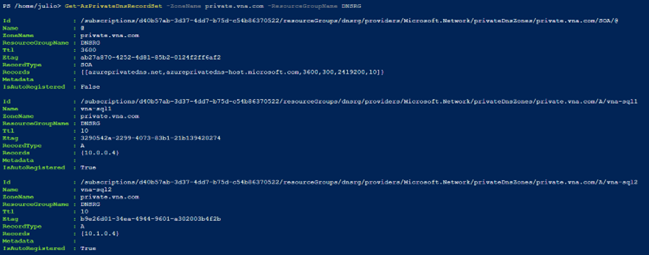
vna-sql1 and vna-sql2 are already registered in the DNS Private zone.
If we want additional DNS records, we can add them manually:
New-AzPrivateDnsRecordSet -Name newHostname -RecordType A -ZoneName private.vna.com `
-ResourceGroupName DNSRG -Ttl 3600 `
-PrivateDnsRecords (New-AzPrivateDnsRecordConfig -IPv4Address "10.1.0.5")
Testing the private zone
Before:
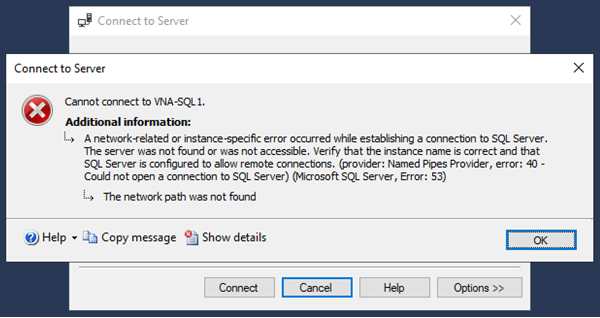
In the image above, I tried to establish a connection to SQL-VNA1 from SQL Server Management Studio (SSMS) installed in VNA-SQL2.
As I mentioned at the beginning of this article, if both VMs were in the same virtual network, the Azure-provided name resolution service would resolve the names automatically. As this is not the case, a network error is displayed.
After:
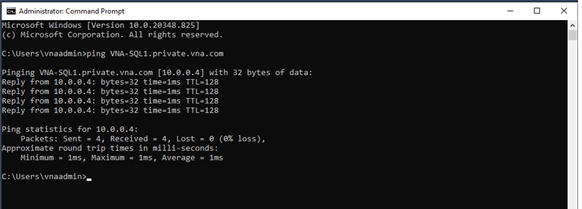
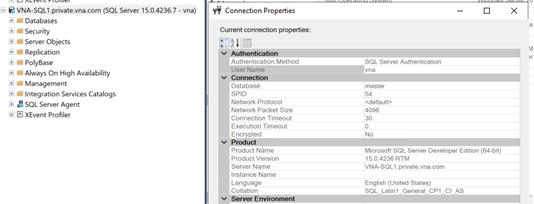
After creating the private DNS resolver service, I’m able to:
- Ping VNA-SQL1 VM from VNA-SQL2 using the hostname plus the private domain name.
- Establish a remote connection in SSMS (in VNA-SQL2) using the hostname plus the private domain name.
Before testing the result, be aware that we must define all the required network rules in:
- Azure VM Networking inbound port rules.
- Local Windows firewall in each VM.3
Summary
Private DNS Resolver is able to do conditional forwarding of domains back to on-premises, across multi-cloud providers, and public DNS servers.
Private DNS Resolver also works with Azure ExpressRoute and Azure VPN solutions.
Private DNS Resolver is not available for all Azure regions yet, for region availability check: private DNS overview.
.png)
.png)
SUBMIT YOUR COMMENT